
In this article, we will focus on the software supply chain and its implementation using Docker Scout. Ensuring the security and integrity of software throughout its lifecycle is crucial in today's interconnected world. Docker Scout is a tool that aids developers and security teams in managing and safeguarding the software supply chain. Among its key features are the analysis of image vulnerabilities and the fixing of application vulnerabilities.
Table of Contents
- Introduction to Software Supply Chain
- Why is Software Supply Chain Security Important?
- Docker in the Software Supply Chain
- Docker Scout
Introduction to Software Supply Chain
The software supply chain refers to the end-to-end process of producing, testing, packaging, distributing, and deploying software. It's a series of steps that starts with the development of source code and extends to the delivery of a final product or service. Managing the software supply chain efficiently is crucial for ensuring the reliability, security, and timely delivery of software.

Why is Software Supply Chain Security Important?
The software supply chain is a prime target for attackers. By compromising the supply chain, they can gain access to sensitive data, disrupt operations, and even take control of systems.
These days, software dependencies are common for almost every project. While developing software, it's not always necessary to write all functionality yourself, and this is where open source plays a pivotal role with its dependencies. A 2020 report by Synopsis suggests that 99% of codebases contained open sources in 2019. This fact implies that your application likely contains code that was not written by your team, which according to Kaczorowski (2020), can pose significant security risks. The same report by Synopsis (2020) states that 75% of codebases had vulnerabilities as per the 2020 Open Source Security and Risk Analysis report. Such vulnerabilities can generate worst-case scenarios for your production environment since thousands of open source developers potentially have access to your repository. One can only speculate about the potential future implications.
Why is Software Supply Chain Security Important?

Docker in the Software Supply Chain
Docker is a platform designed to make it easier to create, deploy, and run applications by using containers. Containers allow developers to package an application and its dependencies into a single, standardized unit for deployment. Docker containers are lightweight and can run consistently across different environments. Here's how Docker might be integrated into the software supply chain:
Development
- Developers use Docker containers to create a consistent and isolated environment for their applications.
- For example, The Visual Studio Code Dev Containers extension lets you use a container as a full-featured development environment. Workspace files are mounted from the local file system or copied or cloned into the container. Extensions are installed and run inside the container, where they have full access to the tools, platform, and file system. This means that you can seamlessly switch your entire development environment just by connecting to a different container.
Build and Continuous Integration (CI)
- Docker can be used in CI/CD pipelines to build application images, ensuring that the application runs consistently in different environments.
- For example, with CI tools like Jenkins, Travis CI, or CircleCI, you can automate the process of building, packaging, and testing Docker containers to ensure the application runs smoothly.
Testing
Docker containers enable testing in an environment identical to production, reducing the chances of "it works on my machine" issues.
Packaging and Distribution
Docker images serve as a standardized packaging format. These images can be easily distributed, making it simple to share applications and their dependencies.
Deployment
Docker containers provide a consistent environment from development to production, streamlining the deployment process.
Docker Scout
Ensuring the security and integrity of software throughout its lifecycle is crucial in today's interconnected world. Docker Scout is a tool that helps developers and security teams manage and secure the software supply chain.
How Docker Scout Helps Secure the Software Supply Chain
Docker Scout provides a number of features that help secure the software supply chain, including:
- Vulnerability scanning: Docker Scout scans container images for vulnerabilities and provides remediation recommendations.
- Software bill of materials (SBOM) generation: Docker Scout generates an SBOM for each container image, which provides a complete inventory of all the software components in the image.
- Policy enforcement: Docker Scout can enforce policies to ensure that only approved images are deployed to production.
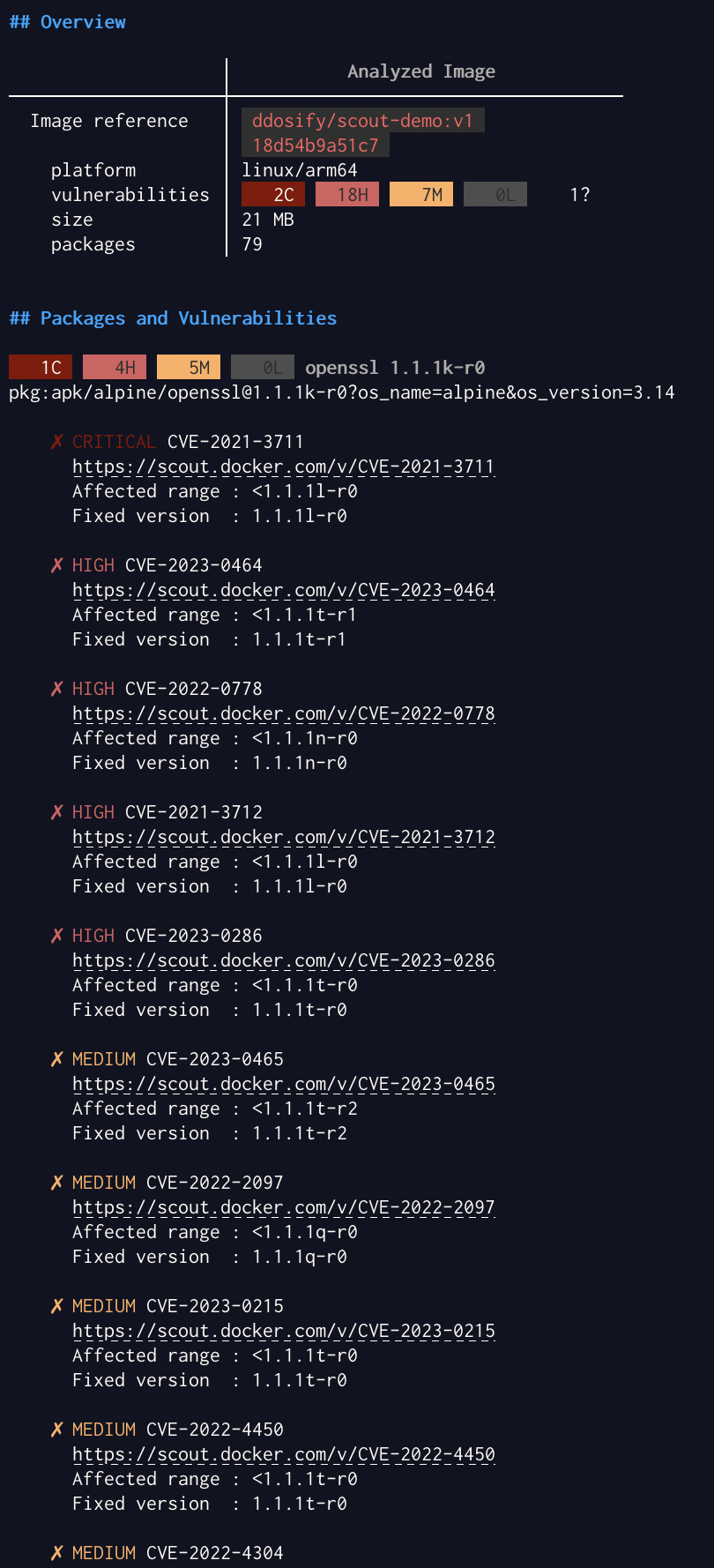
Getting Started with Docker Scout
Docker Scout is included in Docker Desktop 4.17 and later. To get started, Make sure you log in to Docker Desktop or Docker CLI before continuing to the following steps.
Step 1: Setup
We will continue with the Node.js project which contains vulnerabilities in it.
Clone its repository:
git clone https://github.com/docker/scout-demo-service.git
Move into the directory:
cd scout-demo-service
Build the image, naming it to match the organization you will push it to, and tag it as v1:
docker build -t ddosify/scout-demo:v1 .
Create and push the repository on Docker Hub:
docker push ddosify/scout-demo:v1
Step 2: Enable Docker Scout
Docker Scout analyzes all local images by default. Docker Hub, the Docker Scout Dashboard, and CLI helps you to analyze images in remote repositories.
- Sign in to your Docker account with the
docker logincommand or use the Sign in button in Docker Desktop. - Use the Docker CLI
docker scout repo enable [REPOSITORY]command to enable analysis on an existing repository:
docker scout repo enable --org ddosify ddosify/scout-demo
Step 3: Analyze image vulnerabilities
After building, you can use Docker Desktop or the docker scout CLI command to see vulnerabilities detected by Docker Scout.
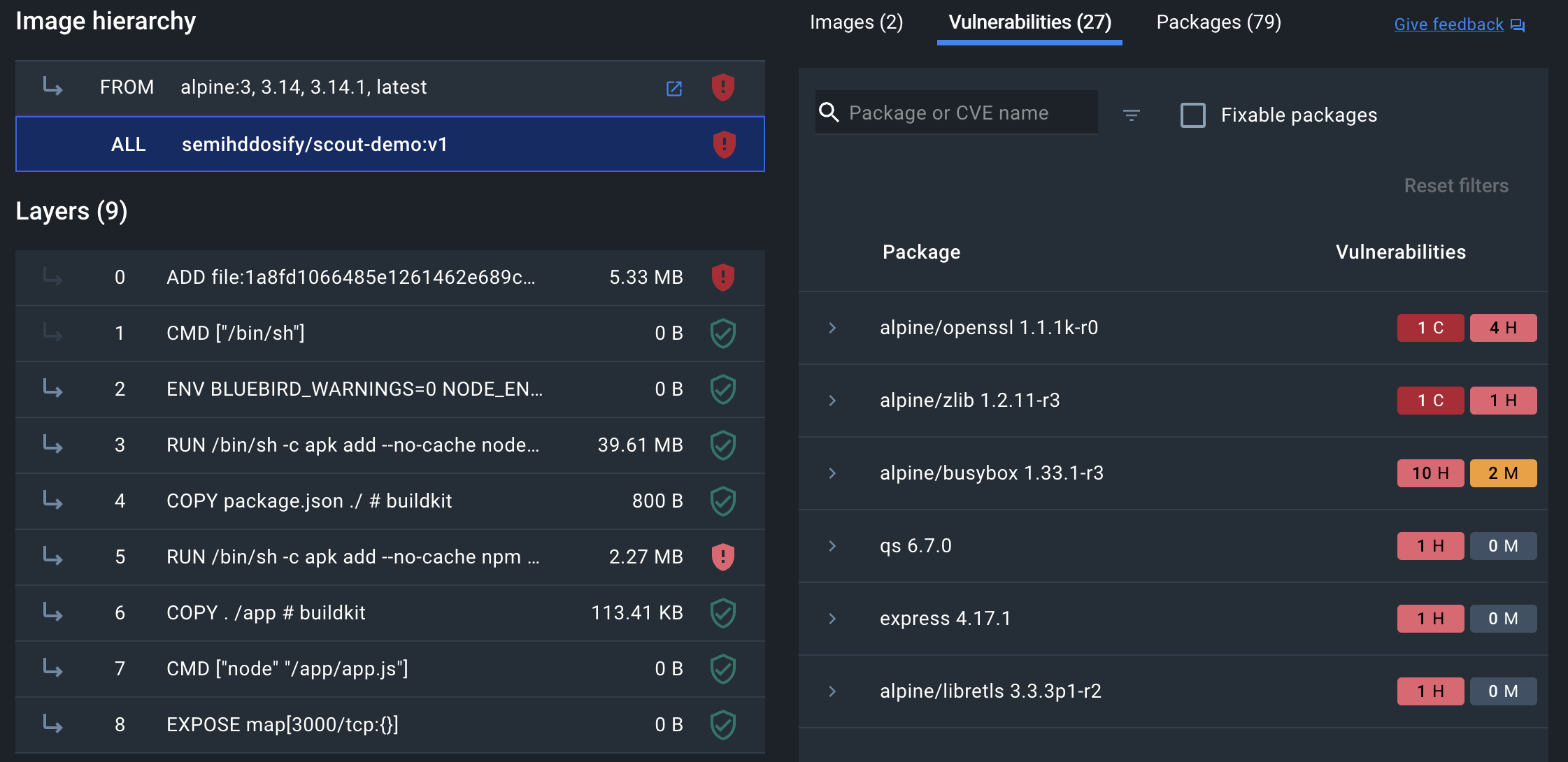
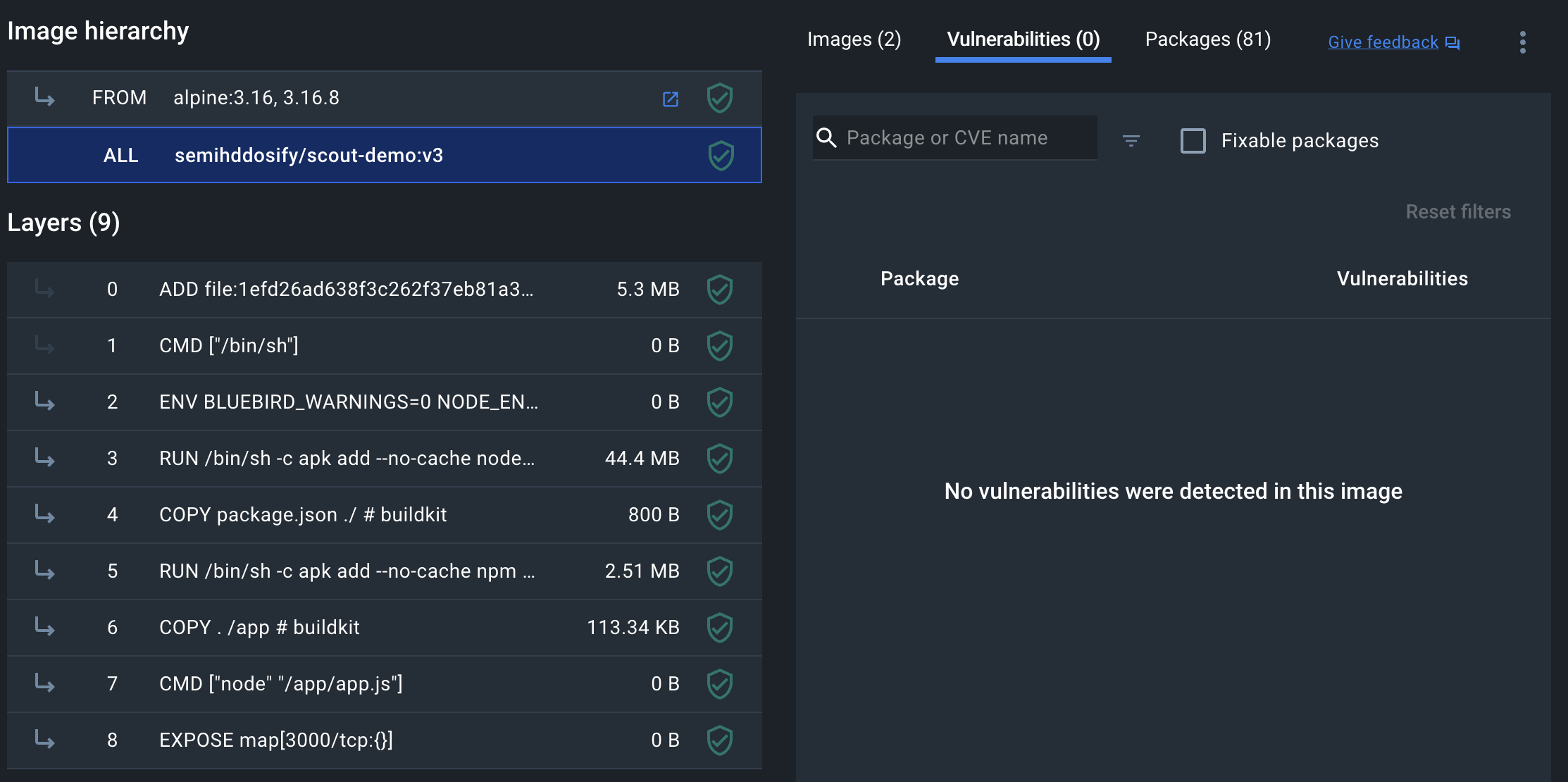
Using Docker Desktop, select the image name in the Images view to see the image layer view. In the image hierarchy section, you can see which layers introduce vulnerabilities and the details of those.
Select layer 5 to focus on the vulnerability introduced in that layer.
Toggle the disclosure triangle next to express 4.17.1 and then the CVE ID (in this case, CVE-2022-24999) to see details of the vulnerability.
Docker Scout Dashboard View
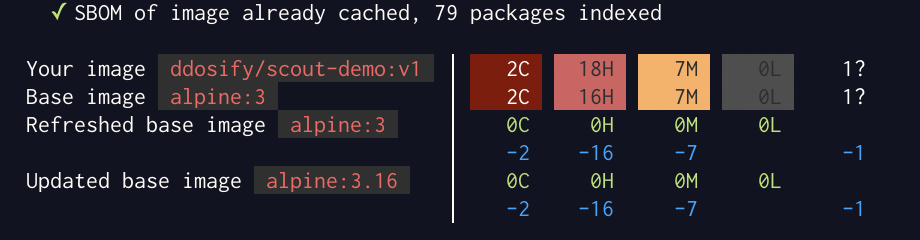
You can also use the Docker CLI to see the same results.
docker scout cves ddosify/scout-demo:v1
Docker Scout Terminal View
Step 4: Fix application vulnerabilities
The fix suggested by Docker Scout is to update the underlying vulnerable express version to 4.17.3 or later.
Update the package.json file with the new package version.
…
"dependencies": {
"express": "4.17.3"
…
}
Rebuild the image, giving it a new version tag:
docker build -t ddosify/scout-demo:v2 .
Push the image to the same repository on Docker Hub using a new version tag:
docker push ddosify/scout-demo:v2
Now, viewing the latest tag of the image in Docker Desktop, the Docker Scout Dashboard, or CLI, you can see that you have fixed the vulnerability.
As you see in the following Docker Scout Dashboard, express version is updated and vulnerability is disappeared from the vulnerabilities list.
Docker Scout Dashboard View
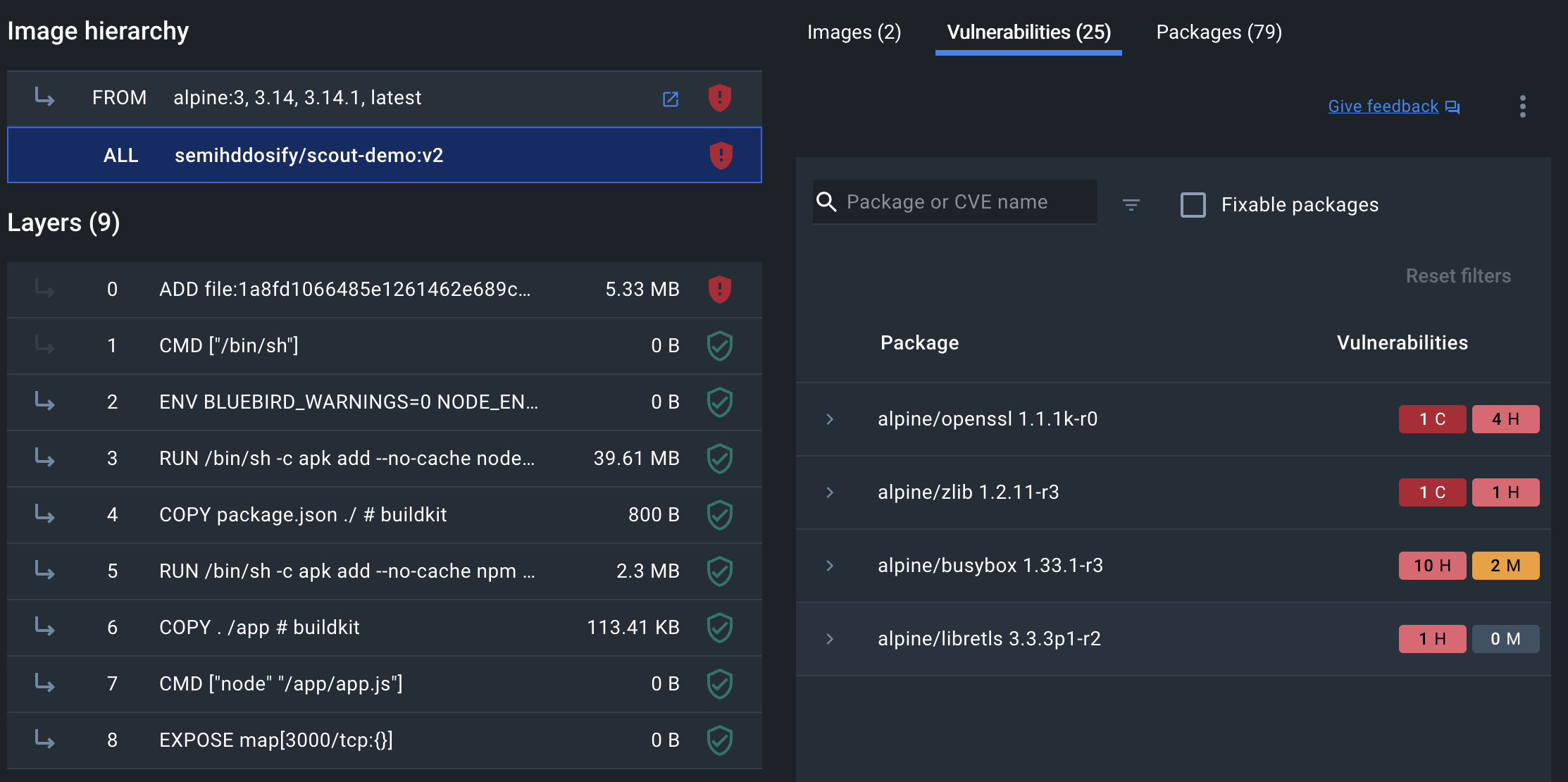
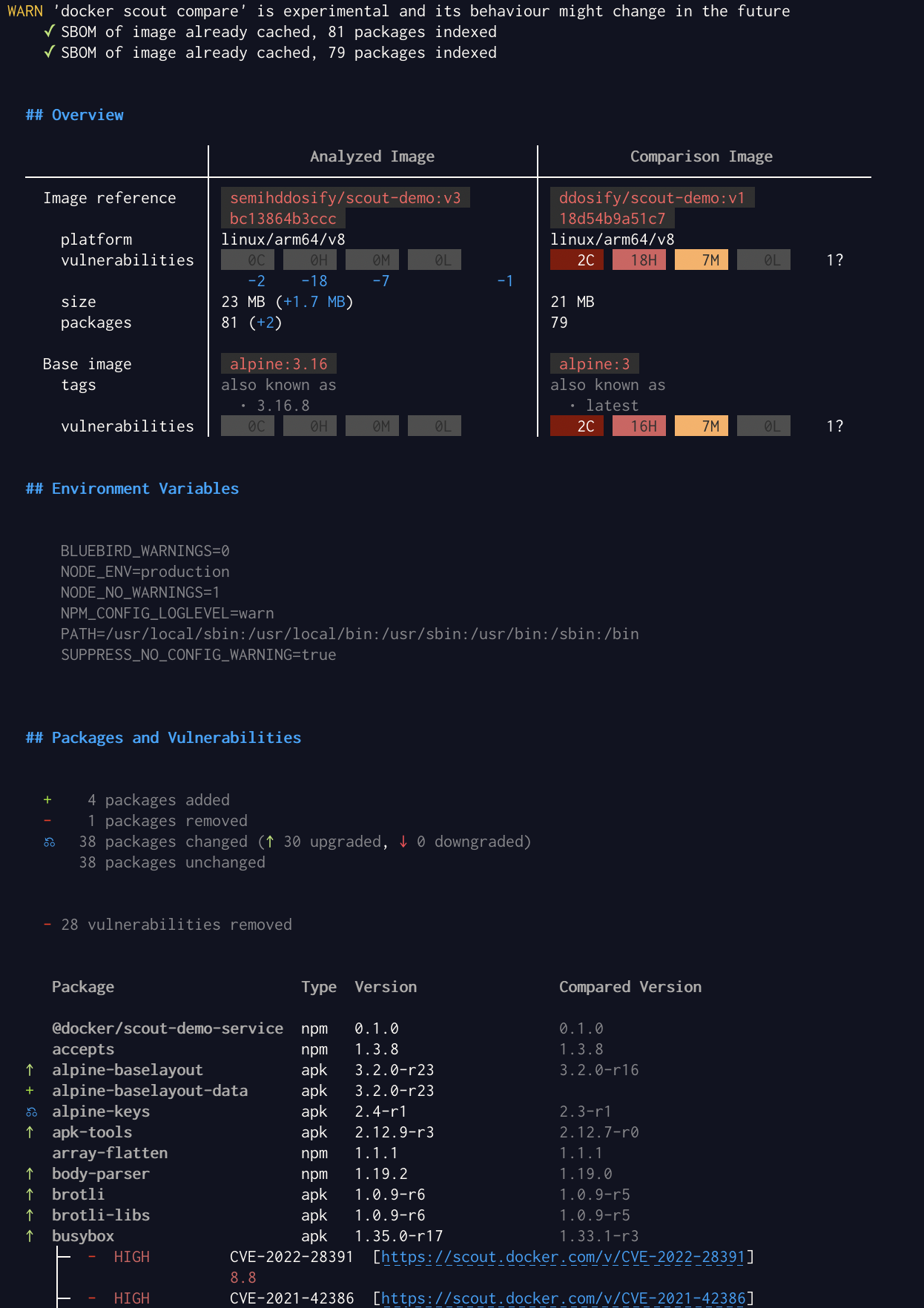
Step 5: Compare images
Use the docker scout compare command to see the compare two image versions. Pass the image that you want to compare as a positional argument to the command, and specify the base image to compare with using the --to flag.
Before compare two images Change base image with Recommended fixes and push it as ddosify/scout-demo:v2. You will see that all the vulnerabilities are fixed.
docker scout compare --to ddosify/scout-demo:v1 ddosify/scout-demo:v2
Docker Scout Terminal Comparison View
Docker Scout Dashboard View
Conclusion
This article provides a comprehensive understanding of the software supply chain and emphasizes the essential role of Docker in it. It begins by explaining the fundamentals of the software supply chain, followed by its significance in terms of security and how Docker integrates into the system. The various stages of Docker, including development, build and continuous integration, testing, packaging and distribution, and deployment, are explained, benefiting developers, testers, and operations. Additionally, this article introduces Docker Scout, a tool designed to enhance the security of the software supply chain, and outlines its functions and a step-by-step guide to its integration, providing readers with a foundation for safeguarding their software supply chain. The aim of this article is to empower the reader with knowledge that will help foster a more secure and efficient software production environment.
Official Docker Scout website: https://docs.docker.com/scout/
For more information please visit this repo. https://github.com/collabnix/awesome-docker-scout
Please note that code blocks and statistics might have changed, so it's crucial to check the official docker website for the latest information. Here are the details based on our research on 5.12.2023.
Resources
Synopsis. (2020). 2020 Open Source Security and Risk Analysis. https://www.synopsys.com/software-integrity/resources/analyst-reports/2020-open-source-security-risk-analysis.html
Kaczorowski, M. (2020, February 2). Secure at every step: What is software supply chain security and why does it matter? https://github.blog/2020-09-02-secure-your-software-supply-chain-and-protect-against-supply-chain-threats-github-blog/
Share on social media: